Nowadays you may face a lot of security issues with different content management systems (CMS) and web applications.Open-source CMS solutions such as WordPress, Joomla and Drupal, have grown very popular amongst many developers. Open-source CMS solutions are seen as affordable, flexible and quick solutions to building a web presence. Unfortunately, the security of this type of software is very average and can result in users having to rebuild their websites, patch up problems that may reoccur or even opt for the safer approach of using a closed or proprietary source CMS solution.
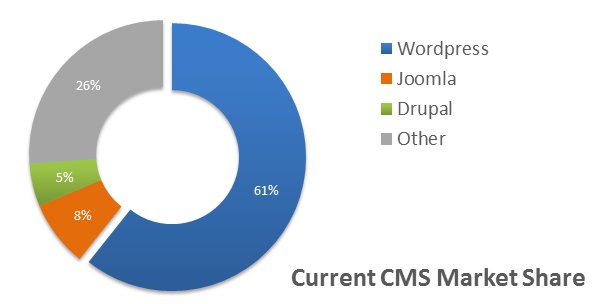
According to statistics from Web Technology Surveys, these three platforms combine to support over 75% of all CMS-powered websites currently online.
They also share another less encouraging similarity: they are among the most common hacking targets on the Internet.
A WP White Security study found that a staggering 73% of all WordPress installations had known vulnerabilities that could easily be detected using automated tools.
Cyber criminals have long discovered these security holes, with over 170,000 WordPress sites being hacked last year.
Why are CMS platforms so vulnerable?
When you consider the different issues in play it becomes obvious why hackers deem CMSes to be appealing targets. It is easy for some to assume that since WordPress, Joomla, and Drupal are such recognizable names, they must be providing some form of protection.
However, the opposite is true. Fact is, CMSes are vulnerable by nature because they are built on open source frameworks. Such shared development environments offer several benefits but they also have their share of flaws, many of which arise form a lack of accountability.
With no price tag, and with no one to take direct responsibility for potential problems, it’s no surprise when the final product has some security issues. Since the top CMSes are so popular, these security vulnerabilities are actively sought after — both by security researchers and members of the hacker community.
Once identified, these flaws can turn into a virtual gold mine for hackers, creating a much more efficient way for them to execute automated mass-scale attacks.
Adding to the issue are website operators who use weak passwords, leaving their admin accounts vulnerable to automated brute force attacks.
In past we’ve showed how such weak passwords were used to inject the website with malware, turning them into DDoS zombies.
Obviously, with administrative access hackers can also deal other kinds of damage: anything from defacing the site (for fun) to using it for malware distribution, which eventually gets it blacklisted in Google and in other search engines.
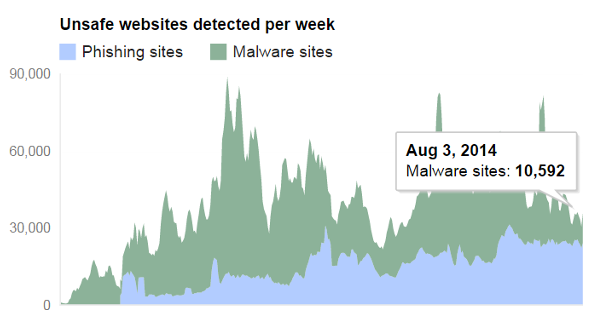
Sites blacklisted by Google on a weekly basis. (Google’s Safe Browsing Initiative)
Finally, there is also the issue of various CMS plugins and themes, which are also exposed to attacks. Each of these is created by a different developer and may introduce an additional set of vulnerabilities.
A recent study found that over 20% of the fifty most popular WordPress plugins were vulnerable to hacking, while a staggering eight million susceptible plugins had been downloaded from WordPress alone.
Considering that most users have at least 3-4 plugins running on their CMS platform, it’s apparent how they can further expose their sites to new security risks.
What we will do?
1.Secure your website
2.Replace error coding with good coding
3.Scan for bugs, exploits and other vulnerabilities
4.Remove malware and dangerous scripts
5.Backup Regularly
Price: Call us today to know about the price of Data Backup service










